Introduction
Apple AirTags are an invention that Apple released to the public on April 30, 2021. There are multiple vulnerabilities that go along with AirTags as well. I will be doing some of my own analysis and seeing how the AirTags really work. This is an Internet of Things (IoT) device that can track whatever the user puts it on. IoT devices in general have been expanding at an alarming rate. The Internet of Things is going to be transforming the future for technology enhancements, and why not wonder how these IoT devices work and communicate with other devices out in the world.
About AirTags
AirTags are developed by Apple Inc. These AirTags are tracking devices for an Apple product. Apple AirTags provide a private and secure way to easily locate the items that are the most important to yourself. They have built in privacy and security features that are able to provide customers with the leverage of power to protect them against the versatility of the iPhone. They are a lightweight design to be smaller, less detectable, and have features such as:
- Built-in speaker to help locate the AirTag
- Removable cover to replace the battery
- Water Resistant
- Dust resistant
- Features a setup just like Air Pods
- Users can assign different names to each item they assign to the AirTag
Screenshot provided below to show the size comparison of an AirTag.

Customers are able to personalize their AirTag as well. They can add features such as:
- Free engravings
- Includes text, and a selection of 31 emojis.
- Polyurethane loops
- Leather loops
- Leather key rings
Apple also provides an easy comprehensive finding experience for their users. Once the AirTag is setup, it will appear in the items tab of the Find My app. Users are able to view the current position of their item they assigned to the AirTag. If a user misplaces or loses the item, they can play a sound that lets the user identify where their item is located. Siri also has a shortcut to help users, all you have to say is “Hey Siri, find my item.” Siri will then locate the AirTag and have the AirTag play a sound if it is nearby.
Users can place their AirTag into lost mode which will help locate the AirTag. Once an AirTag is in lost mode, it will be able to be found by anyone by just tapping on a notification if you are close to the AirTag. I have provided a screenshot below of lost mode option.
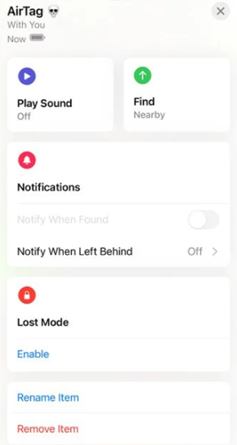
How AirTags Work
AirTags use some of the newest technology such as the U1 chip that is used for Ultra-Wideband. This allows users to enable precision finding for iPhone 11, iPhone 12, iPhone 13, and the new iPhone 14. This new Ultra-Wideband allows a more accurate distance and direction to where the lost AirTag is located when in range of Bluetooth. Screenshot provided below of the enhanced precision finding of Ultra-Wideband.

Once the tag is setup with your Apple id, the tags location will be able to be located on the Find My app. Each tag that is setup, transmits a Unique Identifier (UI) using Bluetooth. The AirTags use Bluetooth Low Energy (BLE). Any local enabled Bluetooth device within the range of 100 meters will then relay this Unique Identifier to Apple’s servers, along with the locational data. The AirTags do not have any locational power themselves, but they essential ping any locally enabled Bluetooth device which then lets the devices locational data do the rest to determine where the AirTag is located.
Privacy
The Apple AirTag is designed to keep locational data private and secure. No physical locational data or locational history will ever be stored in the AirTag itself. The communication between the AirTag and the Find My app will also be end-to-end encrypted so that only the owner of the device is able to access its locational data. The AirTag also has multiple sets of features that help eliminate the urge of unwanted tracking. Bluetooth identifiers are rotated almost frequently to prevent such stalking or tracking. The AirTag also implements multiple safety precautions when the AirTag is not traveling with its owner.
Testing the AirTag
I physically bought an AirTag and had my parents’ setup the AirTag for me. I then took this AirTag back with me to Madison, South Dakota from North Dakota, about 3 hours away. I wanted to see how the process worked when the AirTag was not with the owner. From driving back to South Dakota, it took the whole 3 hours until I was notified that there was an AirTag moving with me. I was first notified with a sound. Then about 20 minutes later, I was notified with a notification that there was an AirTag moving with me, I provided the screenshot below.

I continued to keep driving another 40 minutes with this notification on my phone. I must have cleared it on accident when I got home. Fortunately, after going to work I was able to receive another notification like the above. Once clicking into the notification, I was provided with this screenshot below.
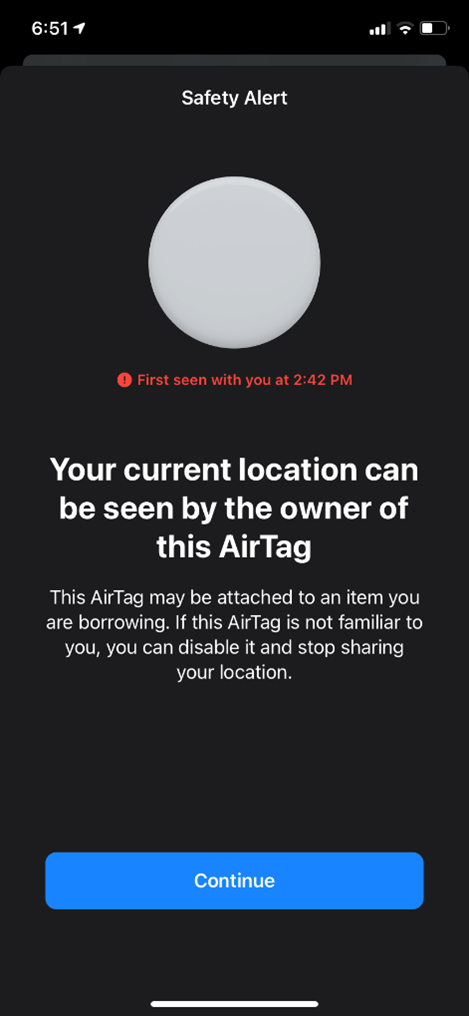
Clicking the continue button brought me to another screen with this information included below:
- Locational data
- Locational history
- When the AirTag was first seen and last seen
- Play sound
- Pause safety alerts
- Learn more about this AirTag
- More information on how to disable the AirTag
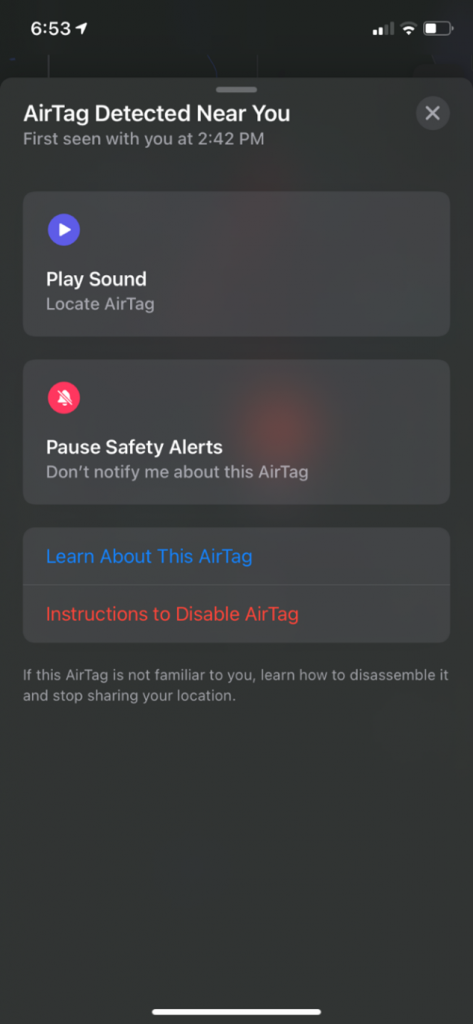
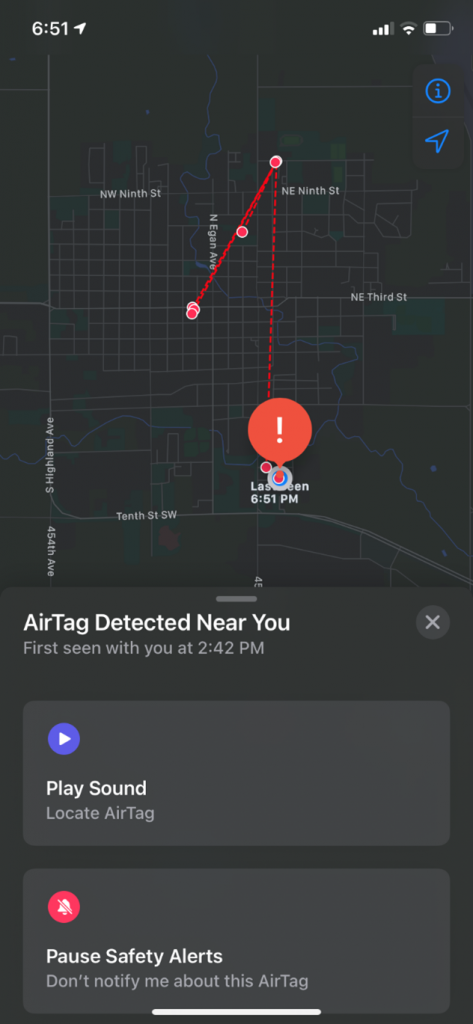
Once done reading the options I quickly clicked on the Learn About This AirTag option. This yielded me another screen which I have provided below.
Once I was able to get the AirTag scanned it provided me with the information below.
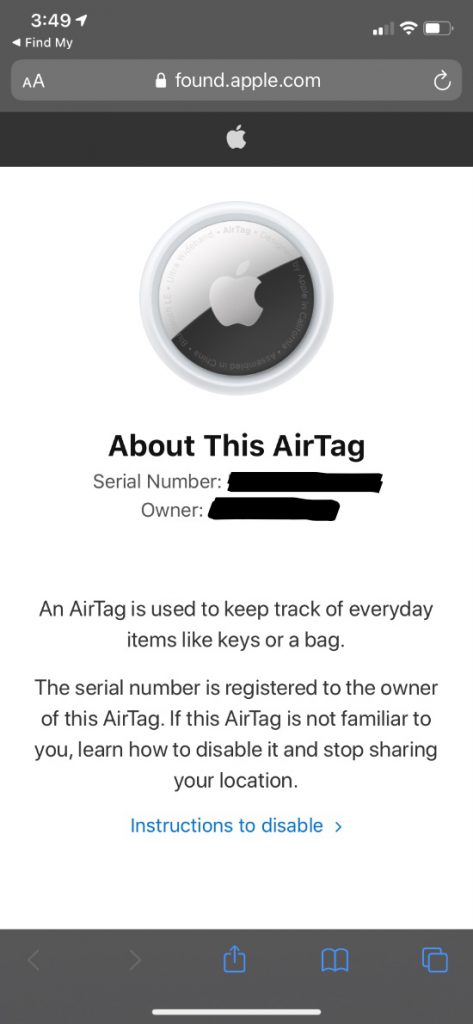
As you can see above, learning about this AirTag can yield not much information but enough information to give you a start to who registered this AirTag. You can see above the serial number of the device and, where the black bar is located, is the last 4 digits of the phone number connected to the Apple ID. With this information above, you could potentially go to a higher authority requesting help on determining who has registered this AirTag.
Attacks brought about AirTags
While doing some more research about AirTags I was able to find 3 attacks brought towards the Apple AirTags. First, a technology scientist by the name Thomas Roth, was able to demonstrate the loopholes with Apple’s security features. He was able to reverse engineer the Apple AirTag. He was able to get inside of the firmware and modified the NFC link that was available through the tracking device. After he gained access to the micro-controller of the AirTag, he reprogrammed the AirTag, and put his own custom link when it is in lost mode. He also posted a Twitter video of his process which I will link here, https://twitter.com/ghidraninja/status/1391165711448518658?ref_src=twsrc%5Etfw%7Ctwcamp%5Etweetembed%7Ctwterm%5E1391165711448518658%7Ctwgr%5E%7Ctwcon%5Es1_&ref_url=https%3A%2F%2Findianexpress.com%2Farticle%2Ftechnology%2Ftech-news-technology%2Fapple-AirTag-tracker-hacked-by-a-security-researcher-7309583%2F.
This attack described above, could enhance the capabilities of malware, and other exploitation that attackers may use. The malware capabilities would include:
- The download of a malicious payload once configuring the NFC link correctly
- Credential stealing
- Manipulation of Apple’s lost mode website
This brings me into the second attack which is XXS injection attacks. As of September 29, 2021, security research discovered that the Apple AirTag is vulnerable to code injection attacks. An attacker could do a simple redirection to a cloned iCloud login page that would record the user’s credentials with a keylogger program. With this attack above this could weaponize Apple’s lost mode website, via the AirTag lost mode.
Lastly, there was the attack named the Good Samaritan. When the AirTag is in lost mode this allows the users to get an alert when the AirTag is missing. Setting the AirTag to lost mode generates a unique URL at https://found.apple.com, and allows the user to enter a personal message and the contact phone number. What Apple forgot to do was sanitize the phone numbers. Looking back at the screenshot about this AirTag, we see that the phone number is sanitized, but when it was not sanitized the found user would be able to call the owner no matter what. With the phone number not being sanitized a vulnerability could allow the user to use code injection by changing the original phone number of the AirTag.
Example:
Let’s say someone with an AirTag dropped an AirTag into their bag, and they lost their bag. They set the AirTag to lost mode, and someone scanned the AirTag to get the information. With this unsensitized phone number, a bad actor could code inject the phone number and change the value of the phone number which could lead to malicious purposes. This thankfully has been patched and fixed.
Conclusion
In conclusion, the Apple AirTag is being used more and more every day. In the DigForCE lab where I work, we have seen multiple iCloud settings being used for setting up an Apple AirTag. The Apple AirTag will be extremely useful though when developing new tracking technology, plus this will also help determine multiple vulnerability patches that could also enhance the security and privacy of future technology. Overall, IoT devices like the AirTags, are being developed and used at an astronomical amount these days. Lastly, the use of IoT devices will only get larger in the future of technology.
